Imagine this: A SaaS provider’s customer portal goes down without warning, exposing sensitive customer details due to an unpatched API vulnerability. Within hours, customer complaints flood social media, IT scrambles to diagnose the breach, and panic spreads among account managers. Customers demand answers: “How did this happen?” “What will you do to fix this?” “Can we still trust you?”
This scenario underscores the critical role of customer success in managing SaaS security incidents. It’s not just about preventing churn but fostering transparency, trust, and partnership during crises. For SaaS providers, customer success managers (CSMs) are the frontline defenders of trust, even when they don’t write the code or configure the firewalls.
It’s estimated that up to 60% of small firms go out of business thanks to cyberattacks – meaning the clock is ticking to retain and reassure customers.
In this guide, we’ll dive deeper into the role of CSMs in protecting and communicating with customers regarding SaaS and cybersecurity – and explore a few ideas you may be able to put into practice right away.
The Importance of Security in SaaS: A Customer’s Perspective
To customers, a SaaS security breach represents more than technical failure—it’s a breach of trust. Whether it’s multi-tenant environments, shared cloud responsibility, or improperly secured APIs, customers expect SaaS providers to be proactive, transparent, and accountable. This is especially true for platforms built on a multi-tenant CMS, where multiple clients share the same infrastructure, making strong isolation, permissions, and data-protection mechanisms absolutely essential.
Customers at the end of a SaaS data breach or cybersecurity incident may feel betrayed by the service provider involved. Why didn’t they do more to stop these problems? What’s happened to my data? What happens next? These doubts can erode trust, even if the provider has strong internal security measures. From the customer’s perspective, they see only the outcomes, not the safeguards.
You could have a robust firewall, set up regular penetration testing to evaluate security risks, and train your teams regularly on cybersecurity essentials – and yet, customers can still be wary of how you intend to protect them.
Here are some SaaS-specific challenges:
- API Vulnerabilities: Many SaaS platforms rely on APIs for integrations, but improper access controls or overlooked vulnerabilities can leave customers exposed. Robust vulnerability scanning tools are essential to stay ahead of such risks.
- Multi-Tenant Risks: Shared infrastructure in multi-tenant environments may lead customers to worry about data partitioning and cross-tenant attacks.
- Shared Cloud Responsibility: Misunderstanding roles in securing data (e.g., SaaS providers handling platform security vs. customers managing application-level controls) often leads to gaps in protection.
Even minor breaches can tarnish the perception of a SaaS company, increasing churn risk. To address this, CSMs must take proactive steps to reassure customers and reinforce confidence in their provider. This includes effectively communicating the safeguards in place, providing clear action plans during incidents, and making customers feel supported and valued at every stage.
By ensuring customers know they are protected and heard, CSMs play a critical role in safeguarding not just customer relationships but also the company’s reputation.
The Role of CSMs in Managing SaaS Security Incidents
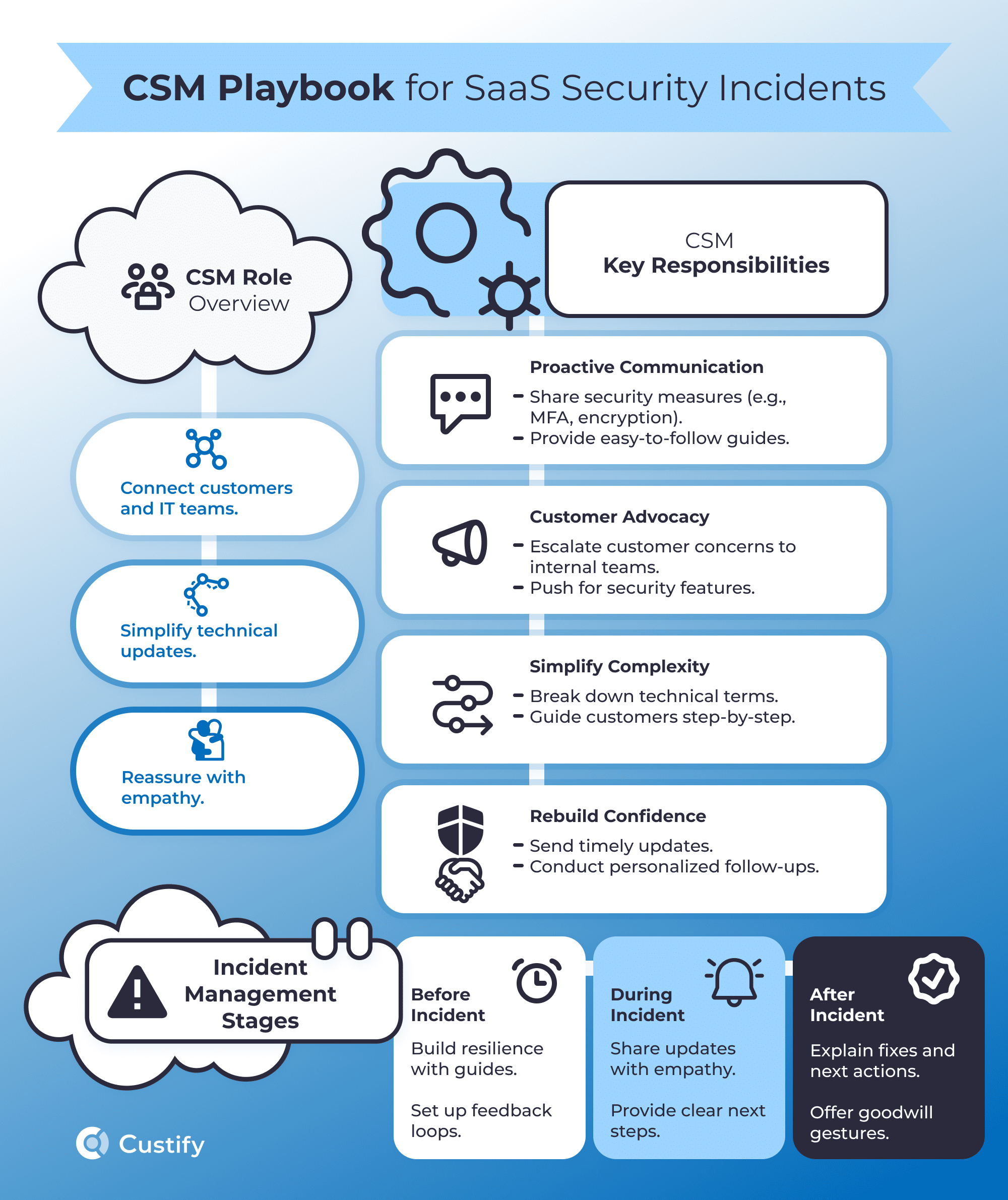
Customer Success Managers (CSMs) serve as the bridge between technical teams and customers during SaaS security incidents. Their primary role is to maintain trust, reduce churn risk, and communicate effectively at every stage. They may not configure firewalls, but they translate technical updates into actionable reassurance for clients.
Key Security Responsibilities of CSMs:
1. Proactive Communication:
- Educate customers about existing security protocols (e.g., encryption, API protection, and role-based access controls).
- Share preventive measures to help customers safeguard their accounts, such as enabling two-factor authentication, implementing identity threat detection and response systems, or monitoring login activities.
2. Customer Advocacy & Collaboration:
- Act as the customer’s voice internally, ensuring that security engineers, product teams, and IT understand their concerns. This means relaying feature requests (e.g., adding MFA options) and escalating concerns about unaddressed vulnerabilities.
- Advocate for customer feedback to influence security upgrades and prioritize fixes.
3. Simplifying Complexity:
- Translate technical jargon into easy-to-understand language for customers.
- Provide step-by-step guidance on actions customers need to take during incidents.
4. Rebuilding Confidence:
- Reinforce the company’s commitment to security with personalized check-ins, transparency, and timely updates.
- Use empathy to connect with customers emotionally, showing accountability and care.
Insights from Cybersecurity CSMs: Balancing Technical and Strategic Roles
Cybersecurity-focused Customer Success Managers (CSMs) operate at the intersection of technical expertise and relationship management. Their responsibilities vary widely depending on the audience they serve, but common themes emerge:
1. Adapting to Varied Customer Needs
CSMs must tailor their approach based on the audience. As one CSM from Reddit noted:
“When I’m meeting with their executives, it’s about goals and value. When I’m working with teams who are hands-on within their organization, it’s all about guidance and education.”
Basically, executives prioritize ROI and overall outcomes, while IT professionals often need technical insights and hands-on guidance.
2. Becoming Product Experts
While CSMs aren’t expected to match the expertise of security engineers, they need a deep understanding of their platform. This knowledge enables CSMs to act as trusted advisors, bridging gaps between technical teams and end-users.
“I’ve never been expected to be on their level of expertise, but I must know which sections do what and how to help the customer get what they need out of the platform.”
3. Advocating for the Customer
CSMs frequently act as liaisons between customers and internal teams, ensuring feedback leads to actionable improvements.
“So much of my time is spent advocating for feature requests, hosting calls with product experts, or firefighting escalations. The key is adding value in every interaction.”
4. Navigating Technical Complexity
Many cybersecurity solutions run “invisibly,” making success hard to measure. Health scores often rely on metrics like software version currency, breadth of deployment, or compliance with updates.
“If your customer isn’t up-to-date, they aren’t secure and therefore aren’t getting value. Adoption in cybersecurity is about ensuring the product is always current.”
5. Managing Escalations with Empathy
In high-stakes environments like cybersecurity, escalations are common. Effective CSMs respond with empathy and clear communication, earning customer trust during stressful times.
“I’ve encountered people who flex their knowledge to test you, but most just want value from the meeting—whether it’s technical advice or a clear next step.”
Through these varied roles, CSMs ensure customers remain confident, even in the face of cybersecurity challenges. Their ability to navigate both technical and relational dynamics is vital in reducing churn.
The Guide to Proactive Customer Success in Cybersecurity
CSMs must anticipate customer concerns and prepare to act decisively before, during, and after SaaS security incidents. Here’s a breakdown:
Pre-Incident Steps: Build Resilience and Confidence
Collaborate with Security Teams: Regularly engage with IT to understand security measures, such as API vulnerability testing, encryption protocols, and monitoring tools.
Educate and Inform Customers:
- Develop simplified guides or videos explaining your security policies.
- Highlight measures like multi-factor authentication, passwordless methods like magic links, and password hygiene.
Create Incident Playbooks: Outline clear action plans for breach scenarios, including customer communication steps, escalation points, and mitigation strategies.
Set Up Proactive Feedback Loops: Use customer feedback to identify security gaps or areas for improvement in user behavior and platform design.
Establish Open Communication Channels: Ensure customers know who to contact for security-related questions and reinforce trust through regular updates.
Mid-Incident Steps: Manage the Crisis with Clarity and Empathy
Coordinate Internally:
- Work closely with IT teams to understand the incident’s scope, impact, and mitigation efforts.
- Clarify timelines for resolution and ensure consistent messaging across teams.
Deliver Timely Updates:
- Notify customers immediately with accurate information about the breach.
- Use empathetic language: “We regret this incident and are working around the clock to resolve it. Your security is our priority.”
Provide Specific Guidance:
- Share steps to mitigate risk, such as:
– Resetting passwords.
– Revoking compromised API keys.
– Clearing browser caches. - Offer resources to help customers tighten their own security, like tutorials on device management or by helping them choose a reliable password manager.
Address Different Audiences Effectively:
- Tailor communication to executives (e.g., focus on mitigation plans) versus IT professionals (e.g., provide detailed technical guidance).
Monitor Social Channels: Actively address concerns on platforms like Twitter or LinkedIn to control the narrative and reassure the wider audience.
Post-Incident Steps: Rebuild Trust and Improve Processes
- Follow Up with Transparency: Announce the resolution publicly, detailing the actions taken to fix vulnerabilities and prevent future breaches.
- Reinforce Security Measures: Share improvements made, such as stronger encryption, additional penetration testing, or enhanced monitoring systems.
Personalized Outreach:
Assign account managers to check in with affected customers individually.
Offer tailored solutions to help them regain confidence, such as security consultations.
Solicit Feedback and Act on It:
Conduct post-incident surveys to understand customer concerns and use insights to refine incident response plans.
Share customer feedback with internal teams to prioritize security enhancements.
Offer Goodwill Gestures:
Extend subscriptions, provide discounts, or grant early access to new features for impacted customers to reduce churn risks.
Document and Reflect: Use the incident as a case study to improve internal processes, ensuring quicker, smoother responses in the future.
Practical Examples of SaaS-Specific Security Scenarios
1. Managing Security Breaches in Multi-Tenant Environments
Problem: A breach impacts only a subset of tenants, leading to confusion and fear among unaffected customers.
Solution:
- Immediately communicate the scope of the breach to all customers, emphasizing which tenants were impacted and why others remain unaffected.
- Example Message: “Following a recent breach, we’ve identified that only tenants with API keys generated before [specific date] were affected. Your account, secured by our updated key rotation policy, remains uncompromised.”
- Proactively share the measures being taken to protect the broader system and offer Q&A sessions for additional reassurance.
2. Utilizing Automated Alerts for Faster Incident Response
Problem: A delay in notifying CSMs and customers about unusual activity leads to prolonged damage and customer dissatisfaction.
Solution:
- Implement automated alerts via tools like Slack, PagerDuty, or Custify that notify CSMs immediately when suspicious activity occurs.
- Workflow Example: If an API shows abnormal traffic patterns, an alert triggers the CSM to review customer accounts and send proactive updates, such as:
“We detected unusual activity linked to your account. As a precaution, we’ve reset your API keys and will guide you through reconfiguration to ensure uninterrupted service.”
3. Explaining Shared Security Responsibility Models
Problem: Customers misunderstand security roles in SaaS setups, leading to gaps in security or misplaced blame.
Solution:
- Develop customer education resources explaining the shared responsibility model. For example, SaaS providers secure the infrastructure, but customers are responsible for proper API key management.
- Proactive Steps:
– Send customers an infographic or video illustrating responsibilities post-onboarding. - – Example Outreach: “To ensure maximum security, please review our guide on API key best practices, including periodic rotation and minimizing unnecessary access permissions.”
- Conduct quarterly security workshops for customers to address common gaps.
4. Responding to API Vulnerabilities
Problem: A vulnerability in the API exposes sensitive customer data, causing panic and distrust.
Solution:
- Immediate Steps: Isolate and fix the vulnerability, then notify customers of the breach scope and resolution timeline.
- Example Communication: “We identified and resolved an API vulnerability that affected [specific time frame]. We’ve revoked compromised tokens and issued replacements. Here’s what you can do to further secure your account.”
- Long-Term: Update API security features with stricter token policies, and inform customers through a detailed product release note.
5. Improving Customer Awareness of Role-Based Access Controls (RBAC)
Problem: A lack of RBAC results in customers granting overly broad permissions, increasing security risks.
Solution:
- Proactively audit customer accounts for permission configurations and notify users of potential risks.
- Example Support Playbook:
– Identify accounts where admin privileges are overly distributed.
– Notify the customer: “We’ve noticed that 80% of users in your account have admin access. Reducing permissions where unnecessary can significantly improve security. Here’s a step-by-step guide to adjusting roles in our platform.” - Include an RBAC check in quarterly business reviews (QBRs) to ensure ongoing compliance.
6. Detecting and Mitigating Phishing Attacks
Problem: Customers fall victim to phishing attempts targeting SaaS login portals.
Solution:
- Immediately notify customers of ongoing phishing campaigns and provide specific guidance to avoid compromise.
- Example Communication: “We’ve identified a phishing campaign impersonating our login portal. Please ensure you only use [official URL] to log in. Reset any credentials if you suspect they were compromised. Our security team is monitoring this closely.”
- Provide templates for internal customer education programs to reduce future risks.
7. Handling Delayed Software Updates in Security-Critical Systems
Problem: Customers delay applying critical updates, leaving vulnerabilities open.
Solution:
- Set up automated reminders through a customer success platform like Custify to notify customers of pending updates, emphasizing their importance.
- Example Workflow: If a customer delays an update for 7 days, trigger a CSM action:
“We noticed your account hasn’t applied our latest update, which includes critical security enhancements. Please install it by [specific date] to maintain compliance and security.” - Offer one-on-one walkthroughs for high-priority accounts needing assistance.
Case Studies of Successful Security Incident Management
To demonstrate the positive effects customer success management can have on end users in light of security incidents, consider the following real-life case studies:
- Target: In 2013, the US retail firm lost up to 110 million customers’ details – and was initially admonished for its slow response. However, the company bounced back by reinvesting in customer care and re-establishing trust, placing buyer needs at the heart of the remediation process. It re-strengthened its security measures, too, such as introducing multi-factor authentication.
- OneLogin: The password management company suffered two major data breaches in just one year – leading to major reputational damage. Learning from its initial breach, the firm immediately reassured its customers and repaired damage done on the day of the second attack. This led to a superfast discovery of bugs and defects within just 48 hours – a move that went some way to repairing customer reputation.
- JPMorgan Chase: 2014 saw the US mega-bank suffer an attack that compromised the data of millions of private and business accounts. While initially damaging to its reputation, the firm turned matters around by publicly committing back to its customers, investigating the source of the attack deeply, and pledging an impressive $250 million each year to improve data security.
- Okta (2023): After unauthorized access to customer support tools, Okta immediately informed clients, deployed new security patches, and issued transparent updates to rebuild trust.
- Zoom (2020): Criticized for security flaws, Zoom responded by hiring a CISO, launching end-to-end encryption, and conducting regular public security briefings.
The lessons SaaS providers can learn from these cases are simple: prioritize customers at every stage of incident management and always be transparent and accountable.
Cross-Functional Collaboration
SaaS CSMs must work symbiotically with internal teams, such as:
- IT & Security Engineers: Simplify technical updates for customer-facing communications.
- Product Teams: Advocate for security-focused features, such as granular permission settings or data residency options. Learn more about collaboration between product and CS teams in our dedicated guide.
- Legal & Compliance: Ensure incident responses align with frameworks like GDPR or SOC 2.
Conclusion
Your customers don’t just want you to provide a fantastic service that makes their lives easier and helps to build revenue. They want your reassurance that you offer a safe, conscientious service and have the credentials and proactivity to back up your promises.
In the event of a security breach, some damage is already done. Therefore, you should focus on how to best support your customers after the event to mitigate churn and even boost your reputation in the eyes of the wider public.
Even better, of course, is to set up a robust cybersecurity plan and to make your actions public – be transparent, be reassuring, and offer guidance.




